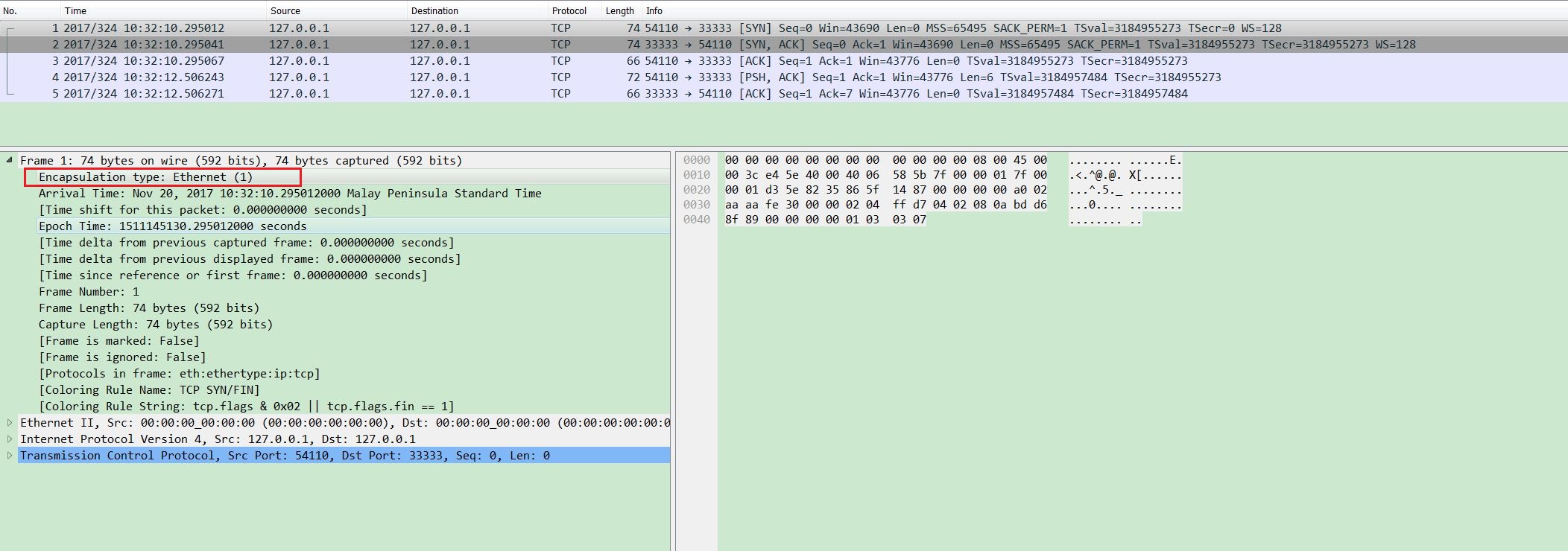
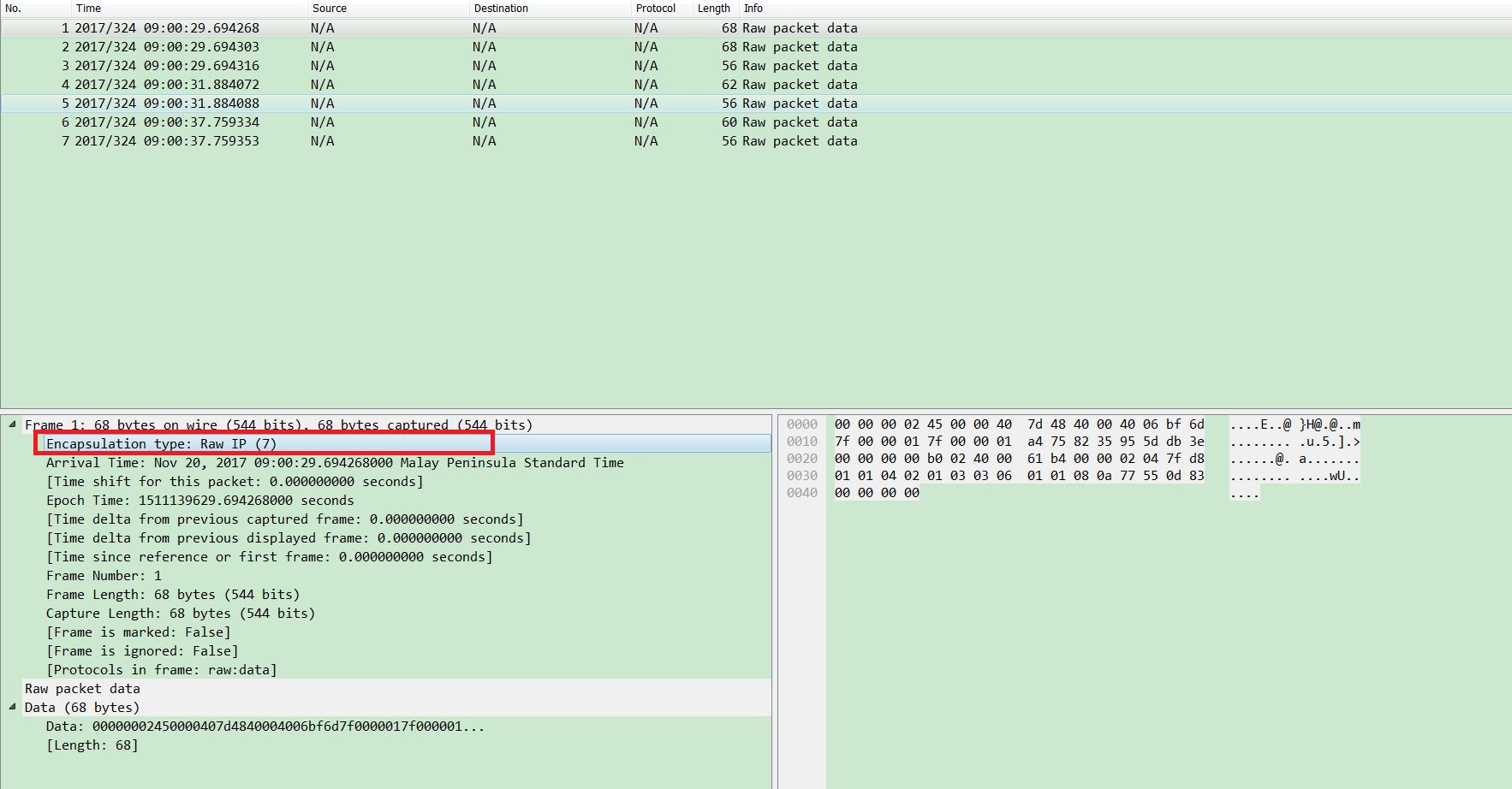
a server program which uses gRPC crashed when started:
$ ./server 60001
......
E1123 15:37:54.133480971 14408 server_chttp2.c:38] {"created":"@1511422674.133408109","description":"No address added out of total 1 resolved","file":"src/core/ext/transport/chttp2/server/chttp2_server.c","file_line":245,"referenced_errors":[{"created":"@1511422674.133405147","description":"Failed to add any wildcard listeners","file":"src/core/lib/iomgr/tcp_server_posix.c","file_line":338,"referenced_errors":[{"created":"@1511422674.133394827","description":"Unable to configure socket","fd":4,"file":"src/core/lib/iomgr/tcp_server_utils_posix_common.c","file_line":200,"referenced_errors":[{"created":"@1511422674.133385167","description":"OS Error","errno":98,"file":"src/core/lib/iomgr/tcp_server_utils_posix_common.c","file_line":173,"os_error":"Address already in use","syscall":"bind"}]},{"created":"@1511422674.133404647","description":"Unable to configure socket","fd":4,"file":"src/core/lib/iomgr/tcp_server_utils_posix_common.c","file_line":200,"referenced_errors":[{"created":"@1511422674.133401558","description":"OS Error","errno":98,"file":"src/core/lib/iomgr/tcp_server_utils_posix_common.c","file_line":173,"os_error":"Address already in use","syscall":"bind"}]}]}]}
Segmentation fault (core dumped)
It is weird because it runs well yesterday. Check the core dump file:
......
Core was generated by `./server 60001'.
Program terminated with signal SIGSEGV, Segmentation fault.
#0 0x00007f30edbbf9b0 in pthread_mutex_lock () from /usr/lib/libpthread.so.0
(gdb) bt
#0 0x00007f30edbbf9b0 in pthread_mutex_lock () from /usr/lib/libpthread.so.0
#1 0x000055c312c87077 in grpc::Server::Wait() ()
......
No clue. So format the above json log:
{
"created":"@1511422674.133408109",
"description":"No address added out of total 1 resolved",
"file":"src/core/ext/transport/chttp2/server/chttp2_server.c",
"file_line":245,
"referenced_errors":[
{
"created":"@1511422674.133405147",
"description":"Failed to add any wildcard listeners",
"file":"src/core/lib/iomgr/tcp_server_posix.c",
"file_line":338,
"referenced_errors":[
{
"created":"@1511422674.133394827",
"description":"Unable to configure socket",
"fd":4,
"file":"src/core/lib/iomgr/tcp_server_utils_posix_common.c",
"file_line":200,
"referenced_errors":[
{
"created":"@1511422674.133385167",
"description":"OS Error",
"errno":98,
"file":"src/core/lib/iomgr/tcp_server_utils_posix_common.c",
"file_line":173,
"os_error":"Address already in use",
"syscall":"bind"
}
]
},
{
"created":"@1511422674.133404647",
"description":"Unable to configure socket",
"fd":4,
"file":"src/core/lib/iomgr/tcp_server_utils_posix_common.c",
"file_line":200,
"referenced_errors":[
{
"created":"@1511422674.133401558",
"description":"OS Error",
"errno":98,
"file":"src/core/lib/iomgr/tcp_server_utils_posix_common.c",
"file_line":173,
"os_error":"Address already in use",
"syscall":"bind"
}
]
}
]
}
Oh, I see. “Address already in use” means the 60001 port is occupied already. I switch to another port, and it works.