I use Meld as code diff and merge tool, but recently I always meet “Invalid byte sequence in conversion input” error in comparing C source code files:
The solution is simple: select “Unicode (UTF-8)” coding:
I use Meld as code diff and merge tool, but recently I always meet “Invalid byte sequence in conversion input” error in comparing C source code files:
The solution is simple: select “Unicode (UTF-8)” coding:
Check the wireshark’s QUIC related code, we will find it heavily depends on 2 macros:
#ifdef HAVE_LIBGCRYPT_AEAD
......
#endif
#ifdef HAVE_LIBGCRYPT_CHACHA20
......
#endif
And these 2 macros rely on the version of libgcrypt (refer here):
/*
* Define HAVE_LIBGCRYPT_AEAD here, because it's used in several source
* files.
*/
#if GCRYPT_VERSION_NUMBER >= 0x010600 /* 1.6.0 */
/* Whether to provide support for authentication in addition to decryption. */
#define HAVE_LIBGCRYPT_AEAD
#endif
/*
* Define some other "do we have?" items as well.
*/
#if GCRYPT_VERSION_NUMBER >= 0x010700 /* 1.7.0 */
/* Whether ChaCh20 PNE can be supported. */
#define HAVE_LIBGCRYPT_CHACHA20
/* Whether AEAD_CHACHA20_POLY1305 can be supported. */
#define HAVE_LIBGCRYPT_CHACHA20_POLY1305
#endif
On CentOS 7, the libgcrypt version is 1.5.3, so the above 2 macros will not be defined, and some functions are not available. While on CentOS 8, the libgcrypt version is 1.8.5, so the functions are fully supported. I met an issue, i.e., for the same pcap file, tshark (I built myself) on CentOS 7 assumes there is an error in decrypting QUIC flow:
$ /home/nanxiao/wireshark/build/run/tshark -nr 435.pcap -Y '(quic.decryption_failed)'
1 0.000000 172.27.232.168 → 216.183.220.159 GTP <QUIC> 1310 Initial, DCID=68a3ee8706f87817
while tshark on CentOS 8 works OK:
$ /home/nanxiao/wireshark/build/run/tshark -nr 435.pcap -Y '(quic.decryption_failed)'
$After upgrading my macOS to Monterey, my Virtualbox’s Void Linux VM can’t connect to Internet through bridged networking, though I can still connect it via SSH terminal emulator. One workaround is changing VM’s network mode to NAT, then configure “Port Forwarding” (Refer here):
(1) Goto Settings -> Network -> Advanced -> Port Forwarding:
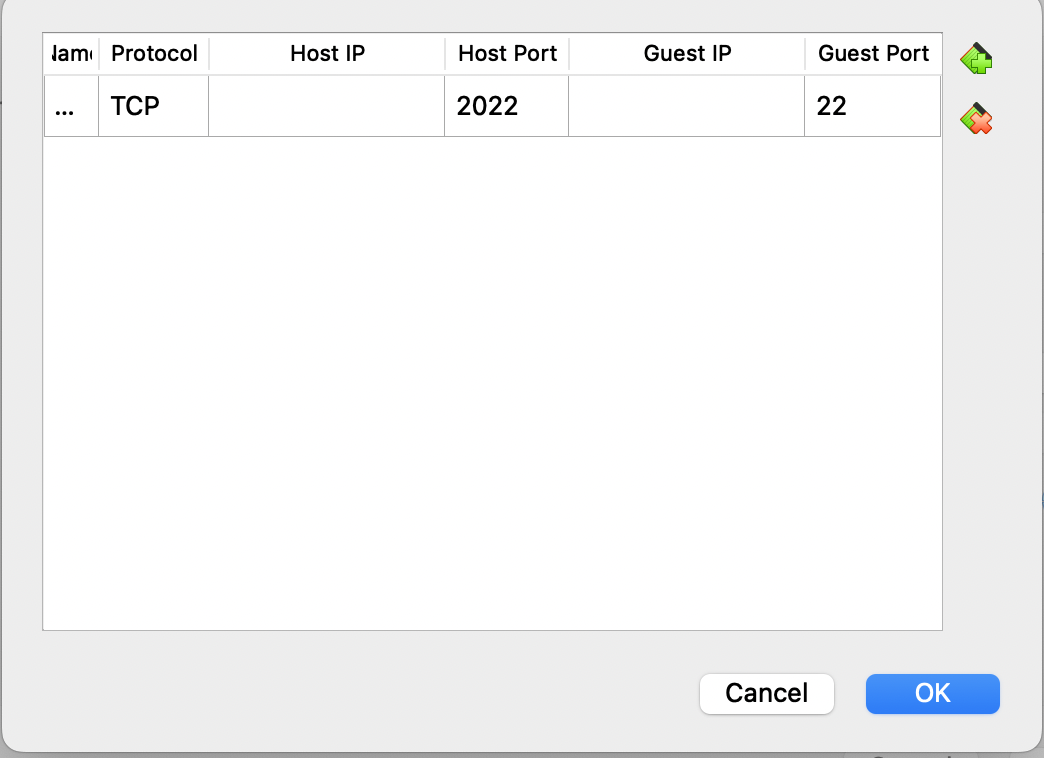
Then “ssh user@127.0.0.1 -p2022” should work.
BTW, for my Void Linux VM, I must modify the nameserver field in /etc/resolve.conf to a public DNS server (e.g., 8.8.8.8):
nameserver 8.8.8.8
Otherwise, I will encounter “Transient resolver failure” error message.
I need to analyse a large pcap file and find problematic packets, so I want gdb automatically outputs packet index when error occurs. Below are the gdb commands:
(gdb) b packet.c:1430
Breakpoint 2 at 0x7ffff0f910aa: file packet.c, line 1430.
(gdb) commands
Type commands for breakpoint(s) 2, one per line.
End with a line saying just "end".
>silent
>frame 10
>printf "frame.number == %zu ||\n", packet_index
>c
>end
(gdb) r
Or you put them in a script:
b packet.c:1430
commands
silent
frame 10
printf "frame.number == %zu ||\n", packet_index
c
end
And it should be handy to log the output for checking later:
(gdb) set logging on