The default shell for OpenBSD is ksh, and it looks a little monotonous:
To make its user-experience more friendly, I need to do some customizations:
(1) Modify the “Prompt String” to display the user name and current directory:
PS1='$USER:$PWD# '
(2) Install colorls package:
# pkg_add colorls
Use it to replace the shipped ls command:
alias ls='colorls -G'
(3) Change LSCOLORS environmental variable to make your favorite color. For example, I don’t want the directory is displayed in default blue, change it to magenta:
LSCOLORS=fxexcxdxbxegedabagacad
For detailed explanation of LSCOLORS, please refer manual of colorls:
# man colorls
......
LSCOLORS The value of this variable describes what color to use
for which attribute when colors are enabled with
CLICOLOR. This string is a concatenation of pairs of the
format fb, where f is the foreground color and b is the
background color.
The color designators are as follows:
a black
b red
......
This is my final modification of .profile:
......
PS1='$USER:$PWD# '
export PS1
LSCOLORS=fxexcxdxbxegedabagacad
export LSCOLORS
alias ls='colorls -G'
......
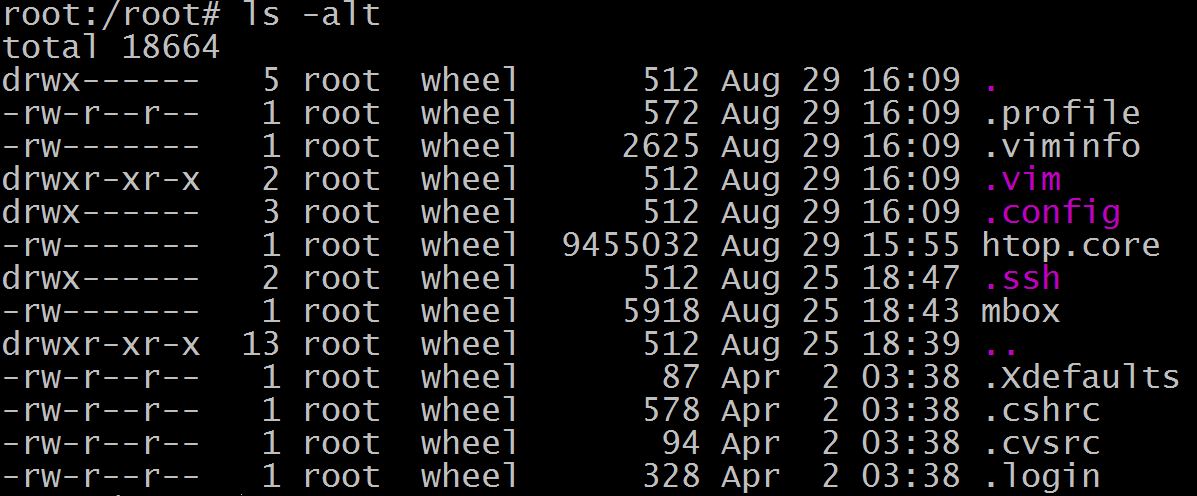
And this is the final effect:
References:
Add Color to Your Terminal;
Why doesn’t alias work in AIX (Korn shell, .profile)?;
ksh.kshrc.