TLS debugging is an awesome introduction of using Wireshark to debug TLS issues (The presentation material can be found here). I just summarise how to decrypt TLS flows here:
(1) Set the filter and capture only TLS flows:
(2) Open chromium and save session secrets in command line:
SSLKEYLOGFILE="$PWD/keys.txt" /Applications/Google\ Chrome.app/Contents/MacOS/Google\ Chrome --user-data-dir=/tmp/cr
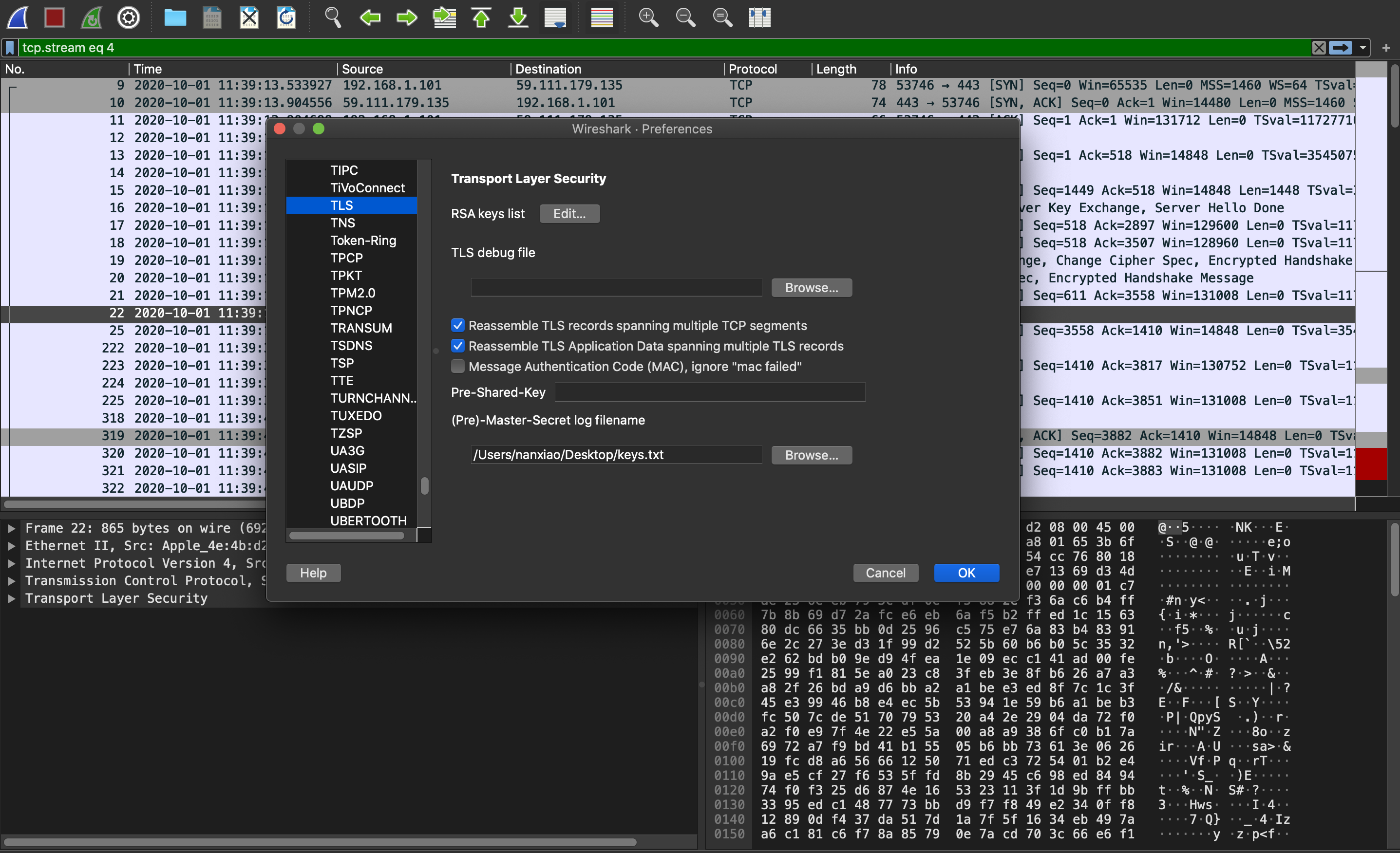
(3)After saving pcap file, Load key and decrypt TLS flows: