Capture the packets on loopback network card on Linux:
# tcpdump -i lo -w lo.pcap port 33333
tcpdump: listening on lo, link-type EN10MB (Ethernet), capture size 262144 bytes
......
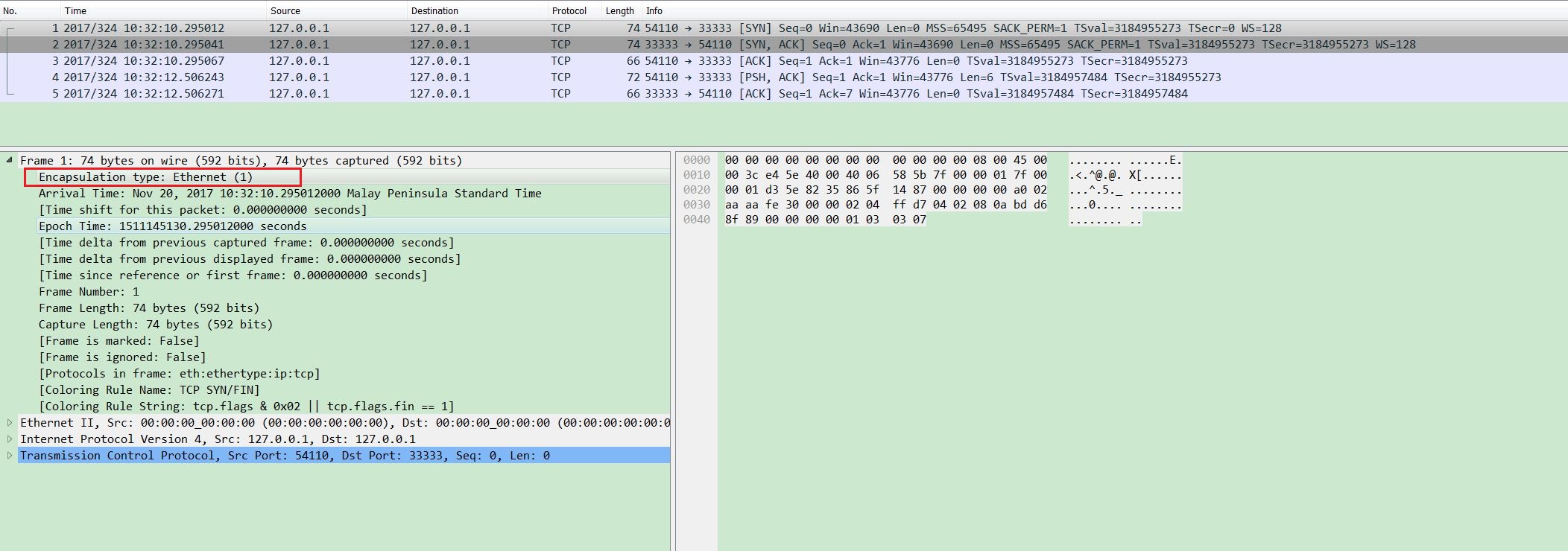
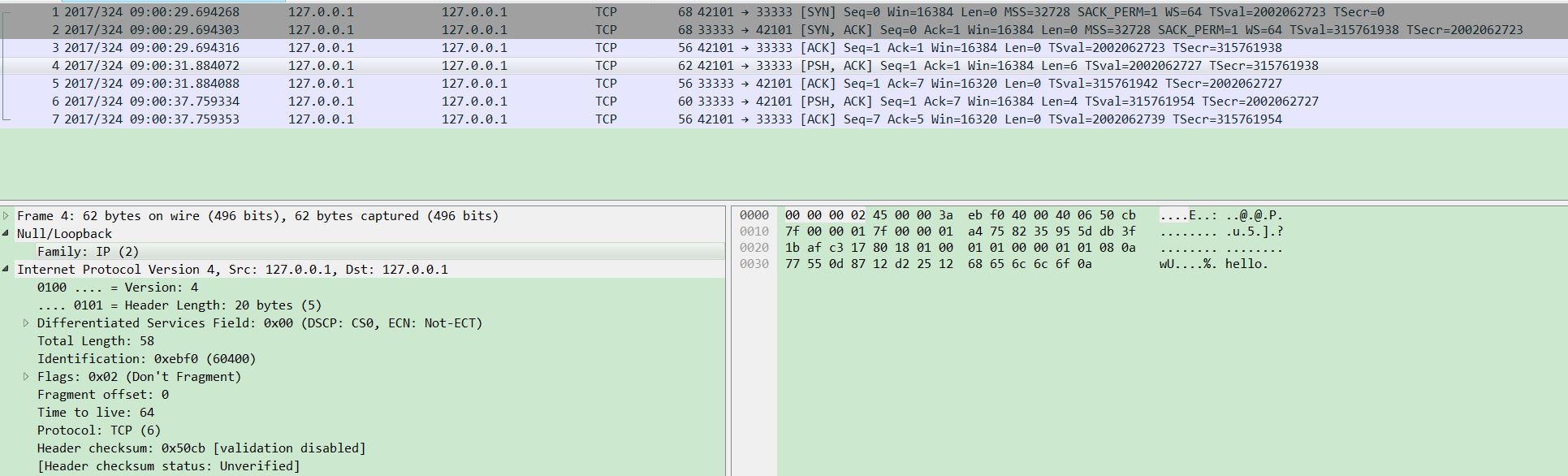
Download it onto Windows and use wireshark to analyze it:
We can see every packet conforms to standard ethernet format.
Capture lookback packets on OpenBSD:
# tcpdump -i lo0 -w lo.pcap port 33333
tcpdump: listening on lo0, link-type LOOP
......
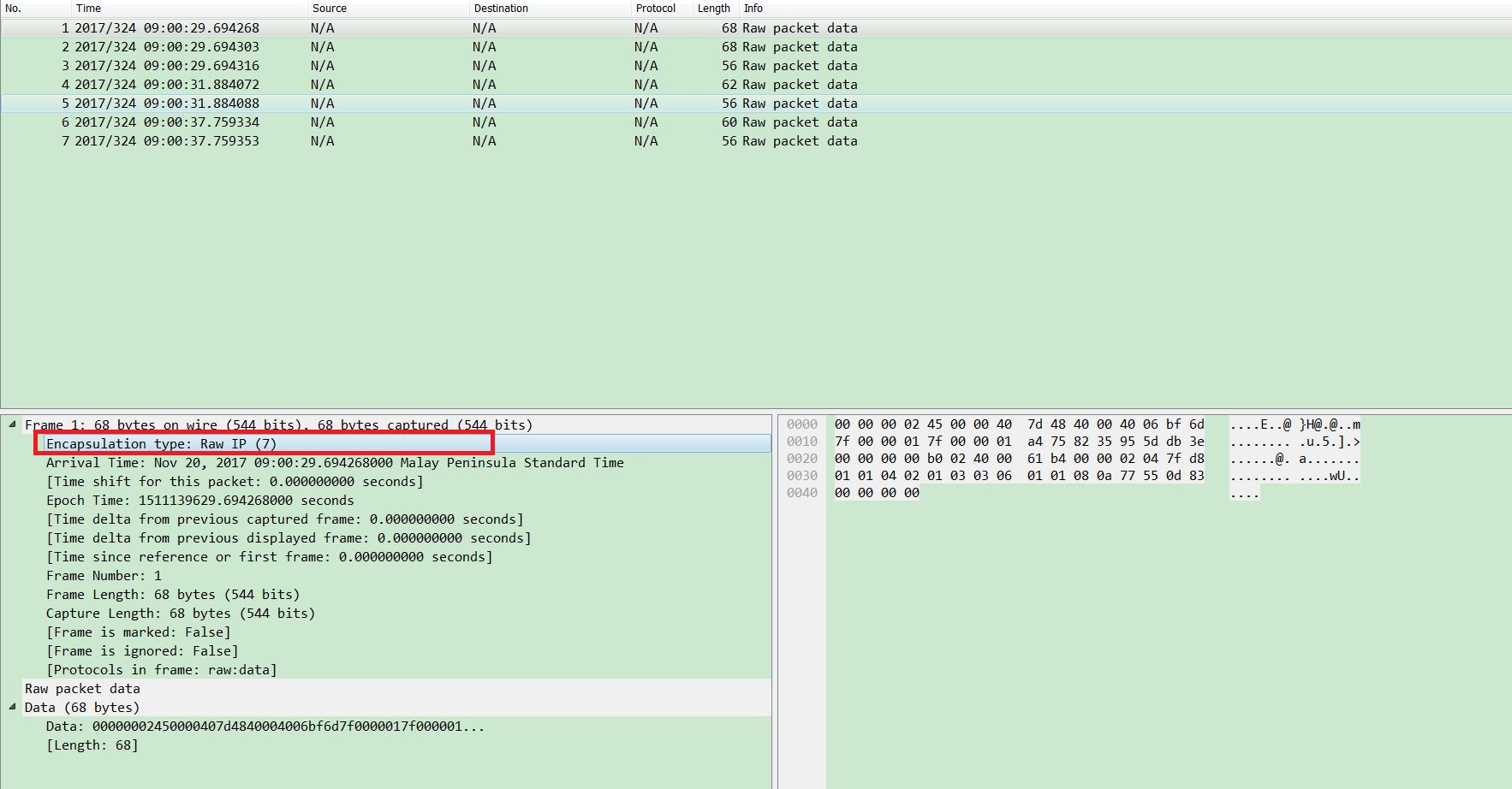
Also download it onto Windows and open it with wireshark:
The wireshark just recognizes the packet as “Raw IP” format, but can’t show details.
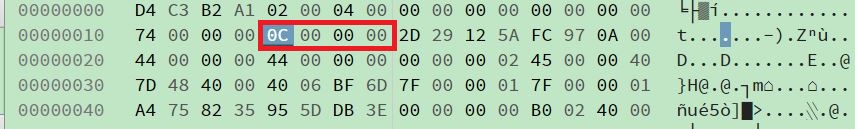
After referring discussion in Wireshark mailing list, I know it is related to network link-layer header type. 0x0C stands for “Raw IP”:
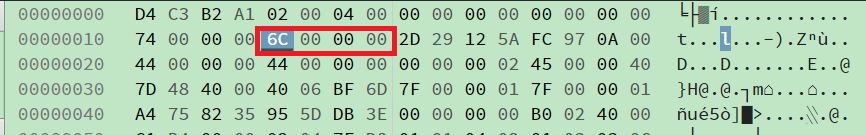
I modified the 0x0C to 0x6C, which means “OpenBSD loopback”:
Now the packets can be decoded successfully:
P.S., I also started a discussion about this issue in mailing list.
Update: I write a script to do this conversion.