Capture the packets on loopback network card on Linux:
# tcpdump -i lo -w lo.pcap port 33333
tcpdump: listening on lo, link-type EN10MB (Ethernet), capture size 262144 bytes
......
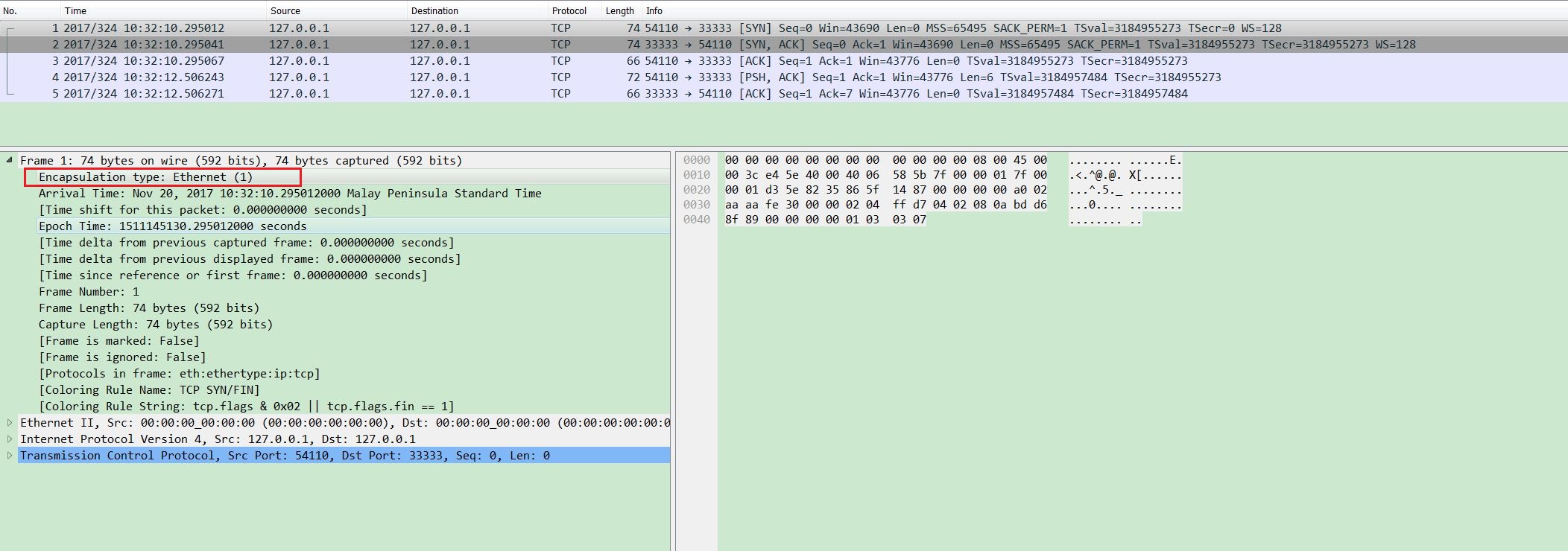
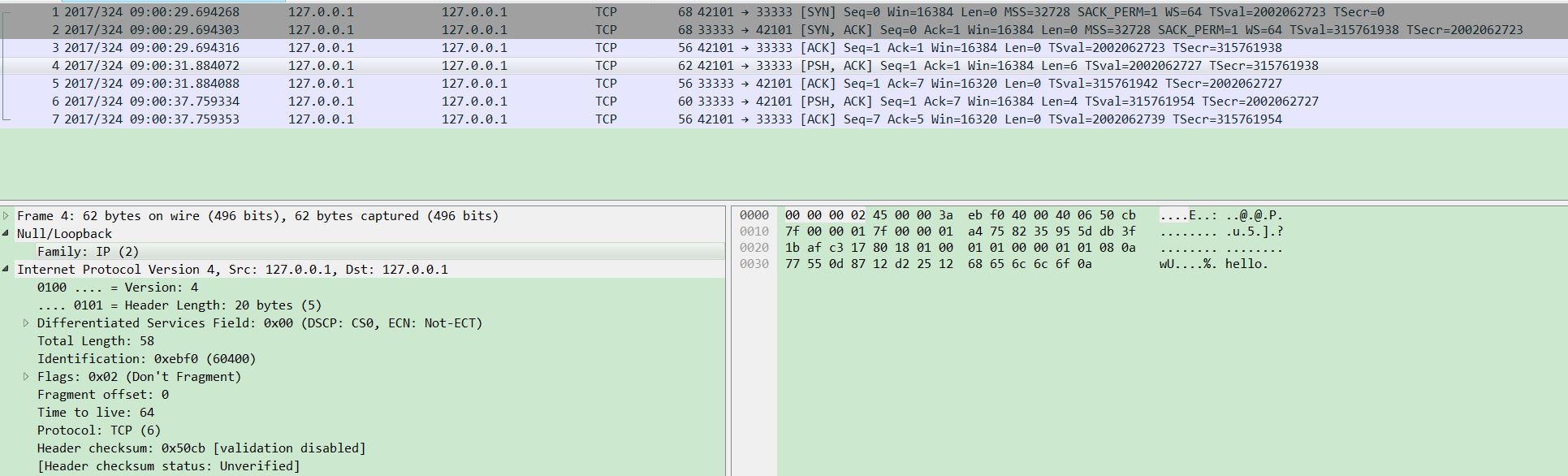
Download it onto Windows and use wireshark to analyze it:
We can see every packet conforms to standard ethernet format.
Capture lookback packets on OpenBSD:
# tcpdump -i lo0 -w lo.pcap port 33333
tcpdump: listening on lo0, link-type LOOP
......
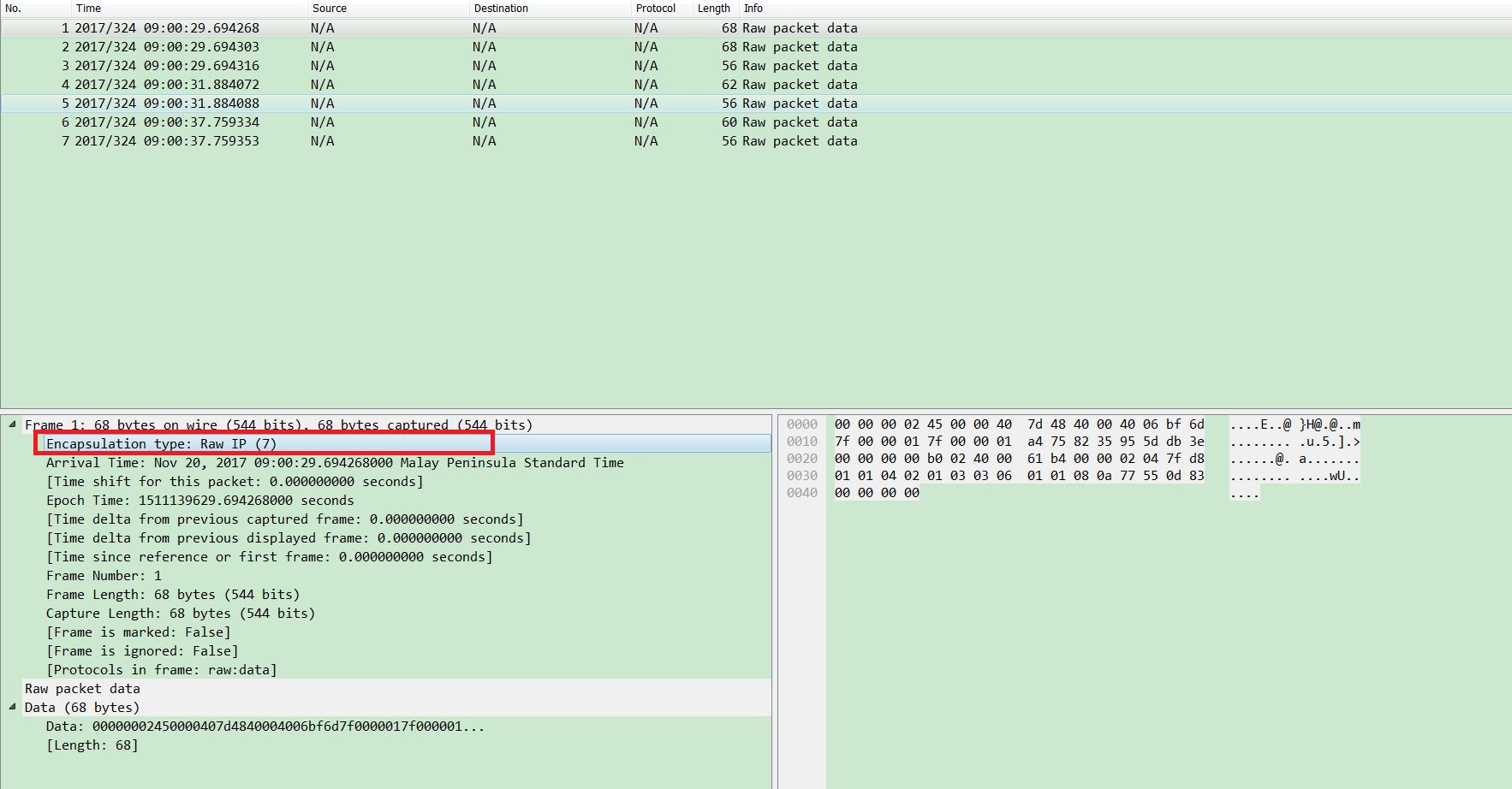
Also download it onto Windows and open it with wireshark:
The wireshark just recognizes the packet as “Raw IP” format, but can’t show details.
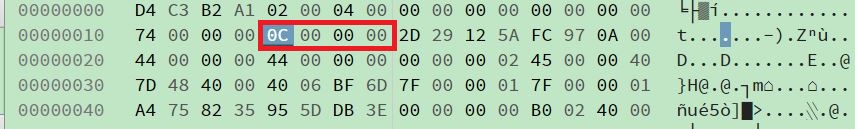
After referring discussion in Wireshark mailing list, I know it is related to network link-layer header type. 0x0C stands for “Raw IP”:
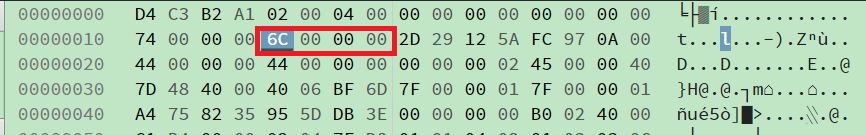
I modified the 0x0C to 0x6C, which means “OpenBSD loopback”:
Now the packets can be decoded successfully:
P.S., I also started a discussion about this issue in mailing list.
Update: I write a script to do this conversion.
Hello Nan Xiao,
I replied to your reddit post at reddit.com/r/openbsd/comments/9a6qkj/the_difference_of_loopback_packets_on_linux_and/ . Do you have any news on this?
Thanks for this blog post.
Hello tryfail,
No any news, thanks!
Best Regards
Nan Xiao
Hello again Nan Xiao,
I worked on this a bit since we last talked here. See my reply at https://www.reddit.com/r/openbsd/comments/9a6qkj/the_difference_of_loopback_packets_on_linux_and/e90mliu
This form was throwing some errors when pasting the python sample here.
Regards